Welcome to my blog. This is a technical site focused on game development. My open-source projects on GitHub: github.com/hxhb and Open-Source projects.
The articles in the blog include a C++ series, Hot Update for UnrealEngine, Plugins and tools development, Game Resource Management series, and thoughts series, etc.
In my spare time, I research and develop technical solutions and preview the results: Showcase. If you are interested in any of the projects, feel free to email me at imzlp@foxmail.com.
In addition to this site, I also created a community-driven Chinese knowledge base site for Unreal Engine https://ue5wiki.com/, hosted on GitHub Pages. Contributions of technical content are welcome to help build the Chinese Unreal Engine technology community! Please see the submission rules: Wiki Content Writing Format and Rules .
 UE as Lib
UE as Lib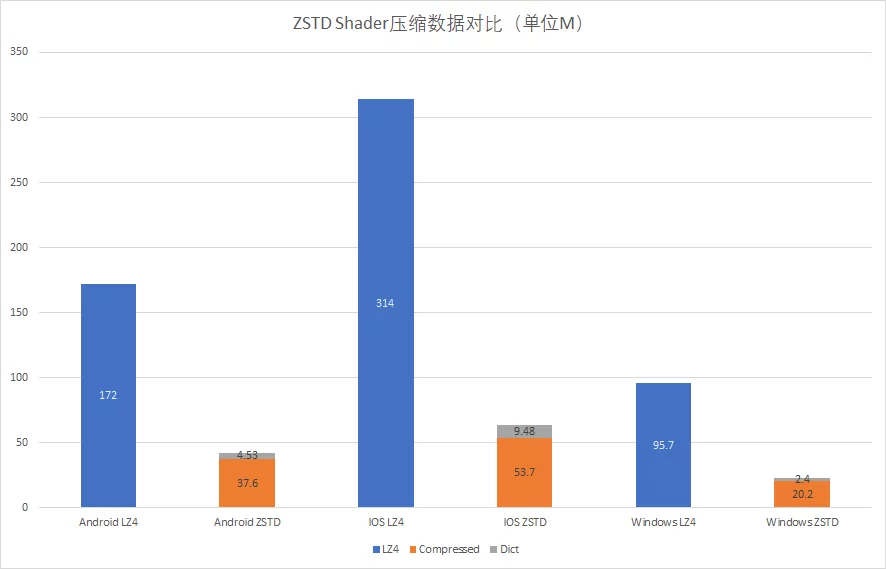 Dictionary-based Shader Compression
Dictionary-based Shader Compression Remake PAK at Runtime
Remake PAK at Runtime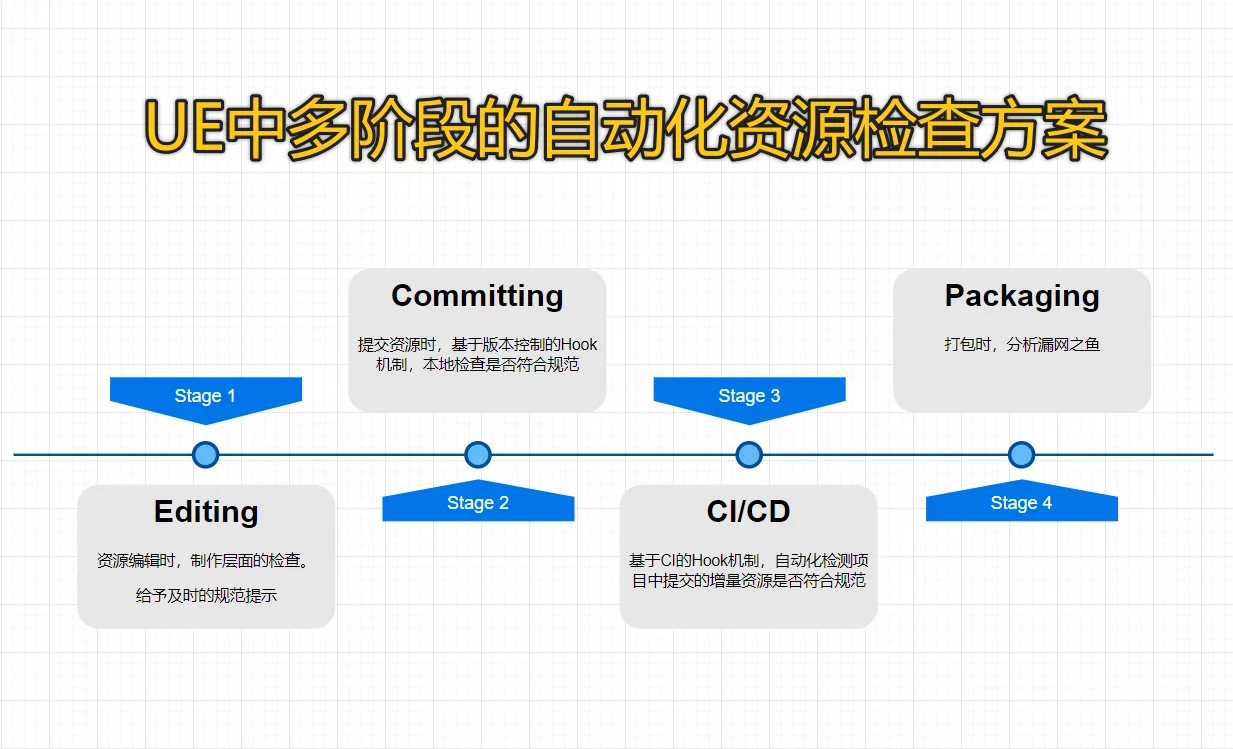 Multi-stage Resource Inspection
Multi-stage Resource Inspection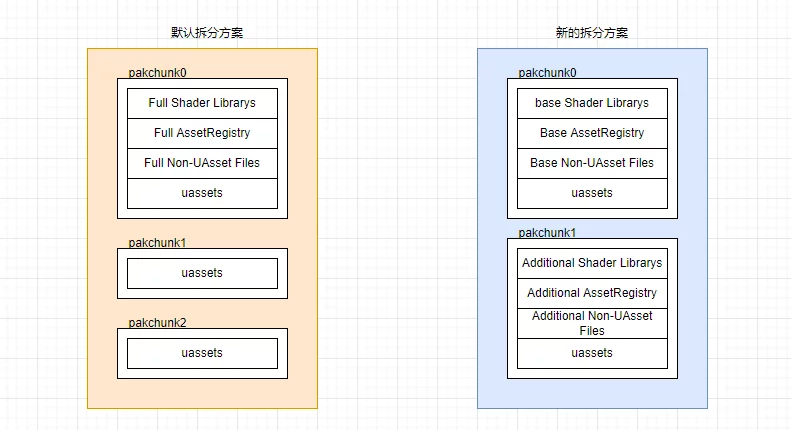 Splitting Game Resource
Splitting Game Resource Human Pose Tracking in UE
Human Pose Tracking in UE